Defender Track
Objective 3: Use jq
Let's start digging into the log data we have. If you don't already have jq installed, you should install it. See https://stedolan.github.io/jq/download/. jq is very useful for digging through json data as we'll see. I will be assuming you are running on macOS, cygwin, or Linux for this guide.
All the logs are in AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/, but often you will have CloudTrail logs in lots of subdirectories, so it's helpful to be able to act on them all at once. Assuming your current working directory is inside a folder where you downloaded these files, and you don't have anything else there, gunzip the files by running the following, which will find all the files in every subdirectory, recursively, and attempt to gunzip them.:
find . -type f -exec gunzip {} \;
Now cat them through jq with:
find . -type f -exec cat {} \; | jq '.'
You should see nicely formatting json data, but it's a lot of info, so let's just see the event names. Replace the jq query in the command above to:
jq '.Records[]|.eventName'You should see:
... "GetObject" "GetObject" "GetObject" "GetObject" "ListBuckets" "AssumeRole" "AssumeRole"These are slightly out of order, so let's include the time. Replace the jq part with:
jq -cr '.Records[]|[.eventTime, .eventName]|@tsv' | sortYou should see:
... 2018-11-28T23:06:33Z GetDownloadUrlForLayer 2018-11-28T23:07:08Z GetObject 2018-11-28T23:07:08Z GetObject 2018-11-28T23:09:28Z ListBuckets 2018-11-28T23:09:36Z GetObject 2018-11-28T23:09:36Z GetObject
The -cr prints the data in a row, and the |@tsv makes this tab separated. Then it gets sorted by the time since that's the first colunm.
Extending that even further, we can replace the jq part with:
jq -cr '.Records[]|[.eventTime, .sourceIPAddress, .userIdentity.arn, .userIdentity.accountId, .userIdentity.type, .eventName]|@tsv' | sort
You can then copy that into Excel or another spreadsheet which can sometimes make the data easier to work with.
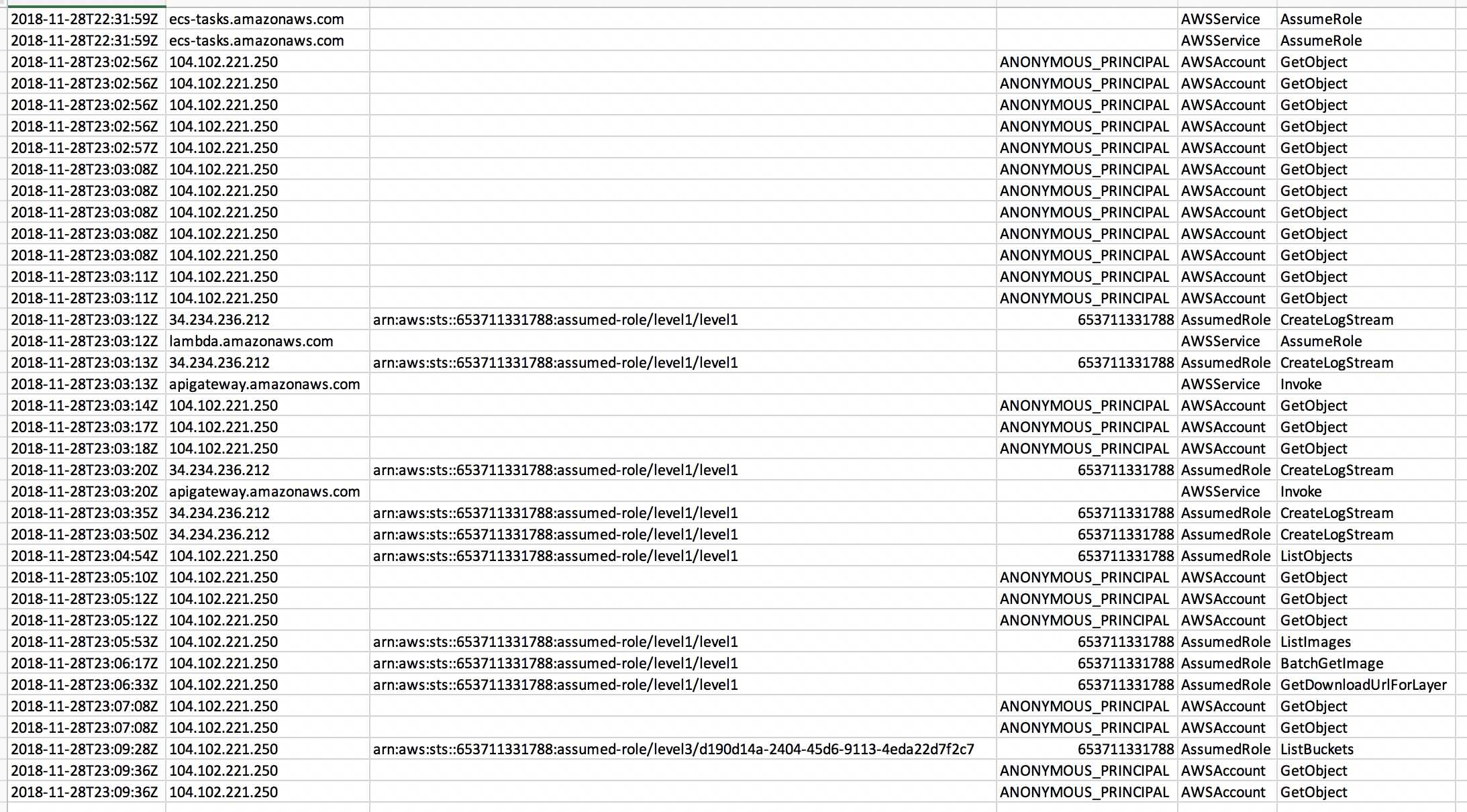
These logs mostly contain the attack, but you'll notice also logs for "AWSService" events as the Lambda and ECS resources obtained their roles. These are logs basically about how AWS works, and not any actions anyone did. There are also a lot of ANONYMOUS_PRINCIPAL, which are calls that did not involve an AWS principal. In this case, these are S3 requests from a web browser. If you look at the user-agent data (.userAgent) you'll see them as Chrome, as opposed to the AWS CLI.