Defender Track
Welcome Defender! As an incident responder we're granting you access to the AWS account called "Security" as an IAM user. This account contains a copy of the logs during the time period of the incident and has the ability to assume into the "Security" role in the target account so you can look around to spot the misconfigurations that allowed for this attack to happen.
The Defender track won't include challenges like the Attacker track, and instead will walk you through key skills for doing security work on AWS. The objectives are:
- Objective 1: Download CloudTrail logs
- Objective 2: Access the Target account
- Objective 3: Use jq
- Objective 4: Identify credential theft
- Objective 5: Identify the public resource
- Objective 6: Use Athena
Credentials
Your IAM credentials to the Security account:
- Login: https://flaws2-security.signin.aws.amazon.com/console
- Account ID: 322079859186
- Username: security
- Password: password
- Access Key: AKIAIUFNQ2WCOPTEITJQ
- Secret Key: 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
Environment
The credentials above give you access to the Security account, which can assume the role "security" in the Target account. You also have access to an S3 bucket, named flaws2_logs, in the Security account that, that contains the CloudTrail logs recorded during a successful compromise from the Attacker track.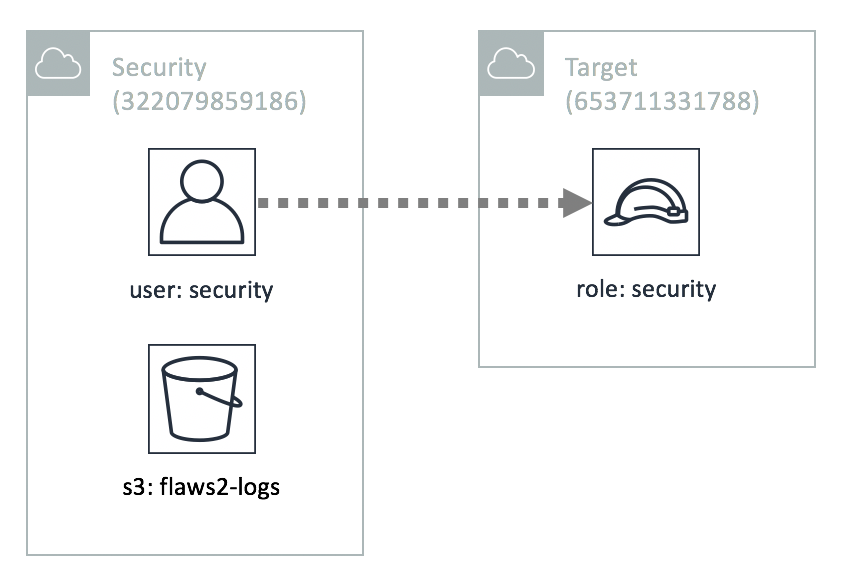
Objective 1: Download CloudTrail logs
Step 1: Setup CLI
The first thing we'll do is download the CloudTrail logs. Do this by configuring the AWS CLI or try using aws-vault as it avoids storing the keys in plain-text in your home directory like the AWS CLI does, so it helps avoid a common source of key leakage.
Ensure this worked by running:
aws sts get-caller-identity
You should get a response back that includes:
arn:aws:iam::322079859186:user/security
You can also run the S3 command to list the buckets in the account (aws s3 ls), and you'll get back flaws2-logs.
Step 2: Download the logs
Now let's download the CloudTrail logs with:
s3 sync s3://flaws2-logs .
You should get a handful of .json.gz files within the directory path AWSLogs/653711331788/CloudTrail/us-east-1/2018/11/28/. These are the CloudTrail logs for a successful hack.
This S3 bucket is public so that you can reference it from Athena later.